Attack paths
Discover attack paths in your Kubernetes clusters that could be exploited
The Attack paths feature in CAST AI is a powerful tool for security teams that helps identify potential security risks in your Kubernetes cluster. It displays a list of detected attack paths that could be exploited by attackers, providing valuable insights into vulnerabilities and exposure points, as well as remediation guidance.
The resources are scanned automatically on your onboarded clusters, so there is no manual scanning involved any time there are changes in the cluster.
NoteThis feature requires enablement of the CAST AI Kubernetes Security. Refer to the Getting started section to enable the Attack paths feature.
What is an attack path?
An attack path is an interactive, visual depiction of one or more potential paths a hypothetical attacker could take to get from the public internet to one of your high-value resource instances.
Identify attack paths
To view attack paths, select Security>Attack paths in the sidebar of the CAST AI console. The attack paths page shows you an overview of all your attack paths that CAST AI detected.
By default, detected attack paths are sorted by their severity level. To change how attack paths are displayed, use the filtering feature or sort the paths by any of the available column headings.
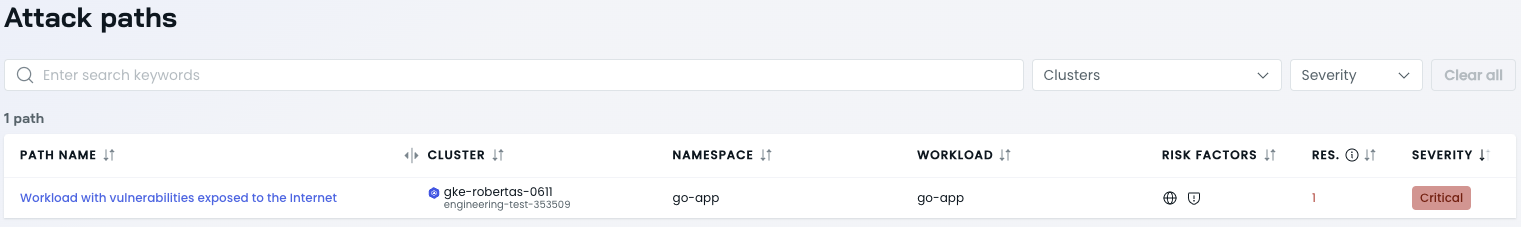
The Attack paths table highlights the following information:
- Impacted cluster
- Impacted namespace
- Workload
- Risk factors
- Number of affected resources
- Severity level: Critical/High/Medium/Low. The severity level of an attack path is determined based on the severity of vulnerabilities in the nodes that comprise it. For example, if an image in the attack path has critical vulnerabilities, the attack path will be equally categorized as critical.
Investigate an attack path
To view the details of an attack path, click on the path name to go into the detailed view.
The attack path details show how the vulnerable application is exposed. In the showcased example below, the vulnerable application is exposed via this path:
- Internet node connected to the
go-appservice go-appservice exposed to the internetgo-appservice exposing thego-appdeploymentgo-appdeployment running the vulnerable image
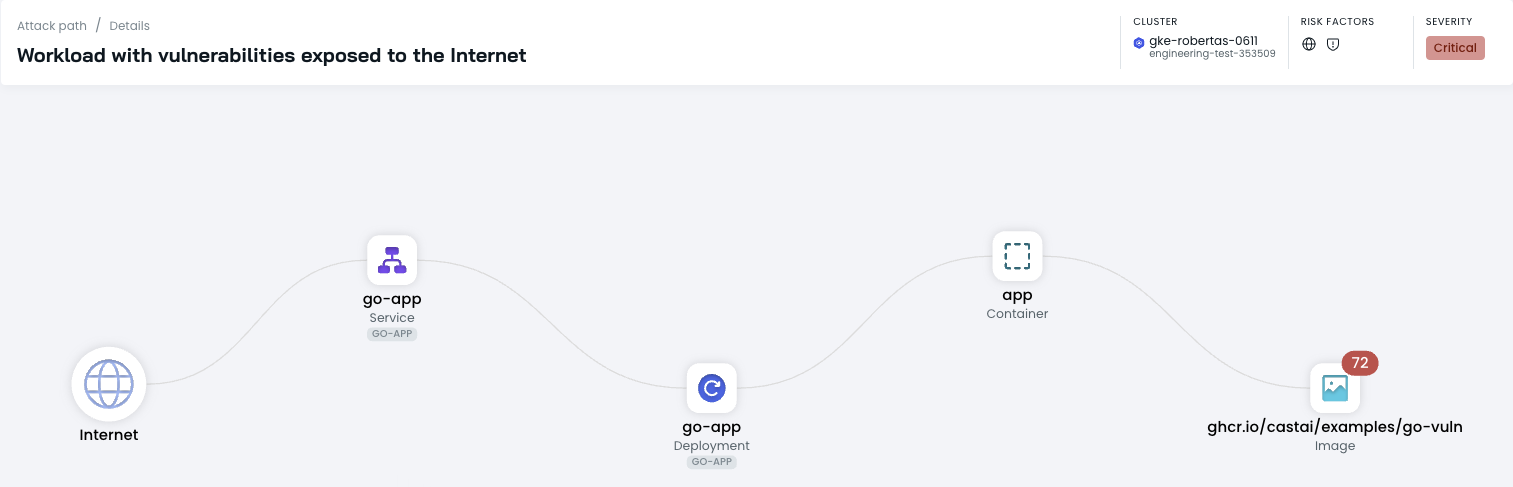
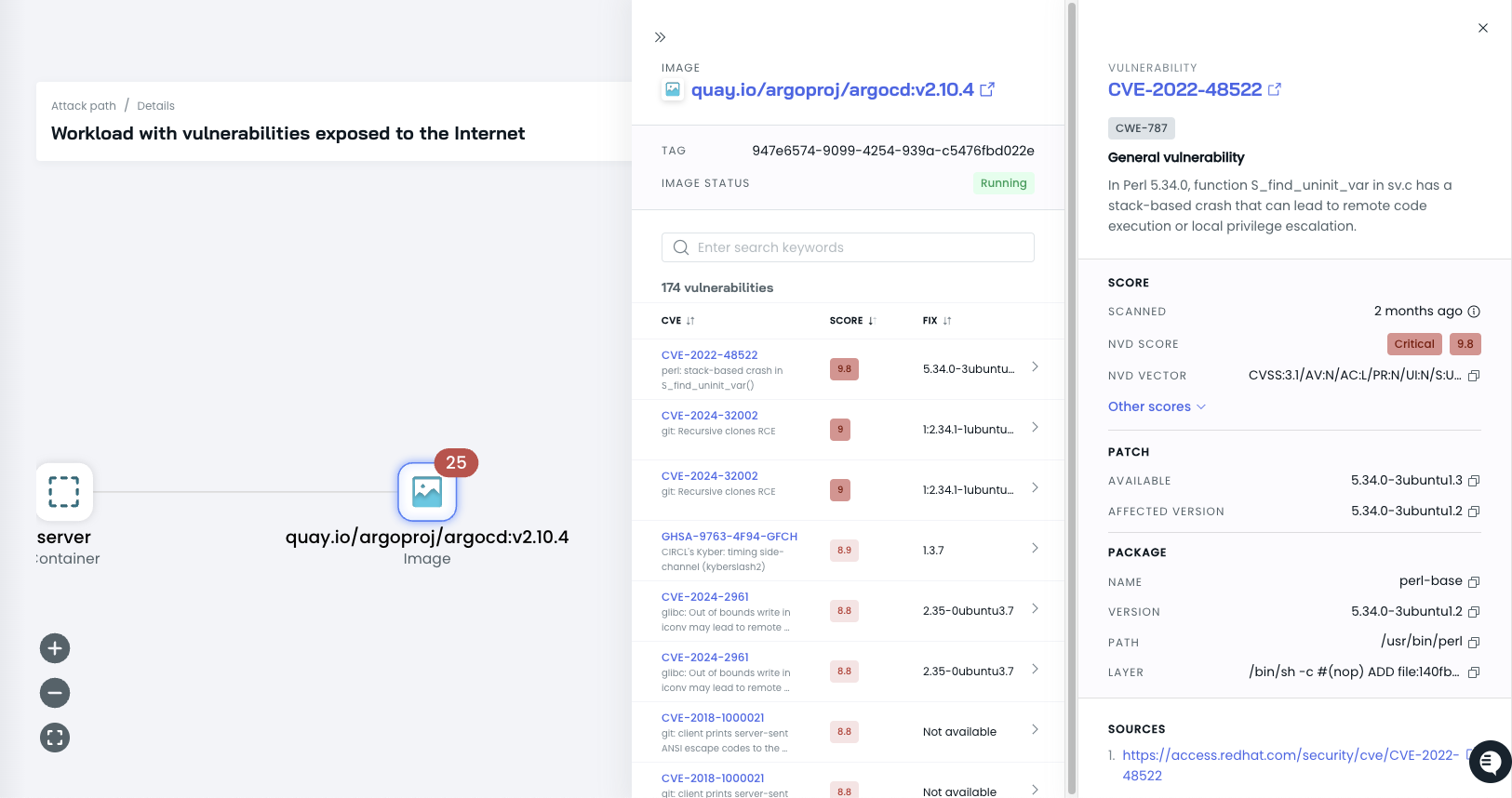
By clicking on the vulnerable image in the attack path, you can access more details about the specific vulnerabilities present in the image.
Display node information
The nodes in an attack path represent the resources on an attack path. You can display more information about each node in an attack path by clicking it.
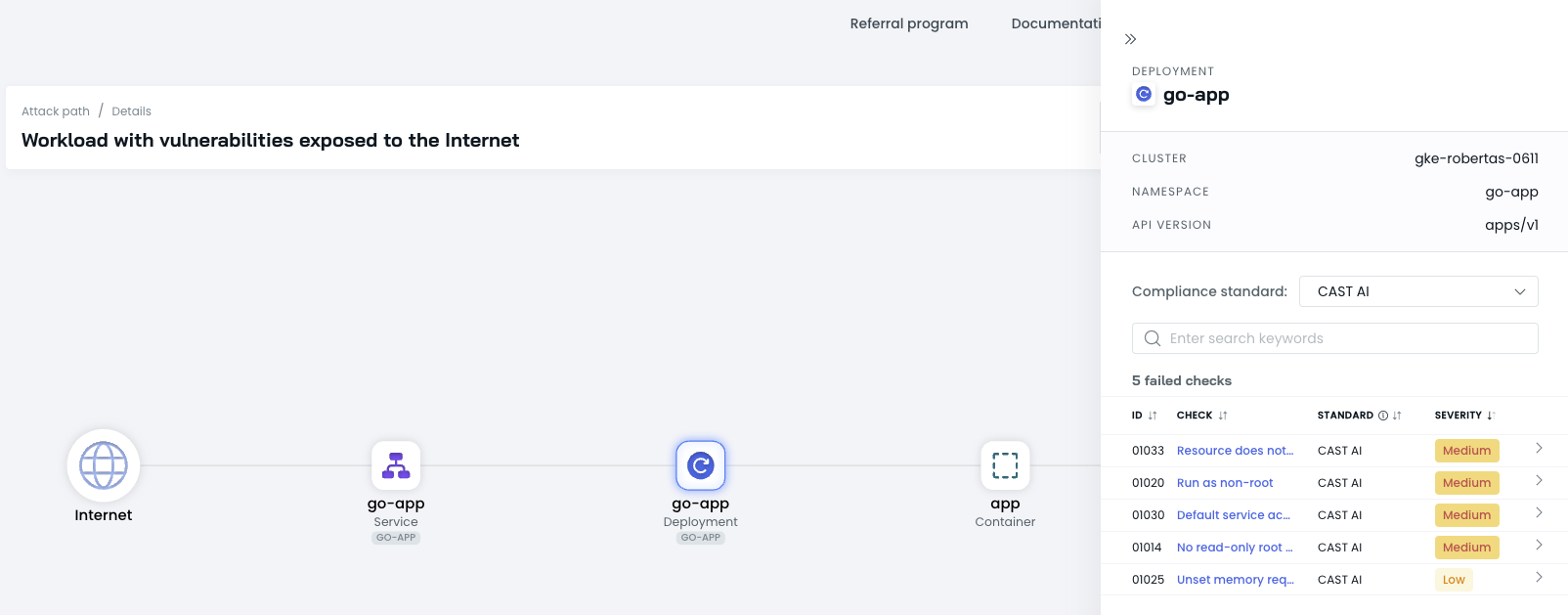
Clicking the resource name in a node displays more information about the resource and any findings that affect it.
Node types
- Internet: Represents the public internet.
- Ingress: Represents a Kubernetes Ingress resource that exposes the vulnerable workload.
- Service: Represents a Kubernetes Service that exposes the vulnerable workload.
- Deployment: Represents a Kubernetes Deployment that manages the vulnerable workload.
- Container: Represents a container running the vulnerable image within the Deployment.
- Image: Represents the vulnerable container image used by the workload.
Attack path lines
In an attack path, lines between the nodes represent potential accessibility between resources an attacker could leverage to reach a high-value resource.
Remediate an attack path
To effectively block or remediate an attack path that exposes a workload to the internet, it is crucial to address the vulnerabilities present in the container image. While preventing internet access to the workload can limit the exposure, it does not resolve the underlying security issues.
To address the vulnerabilities and block the attack path, follow these steps:
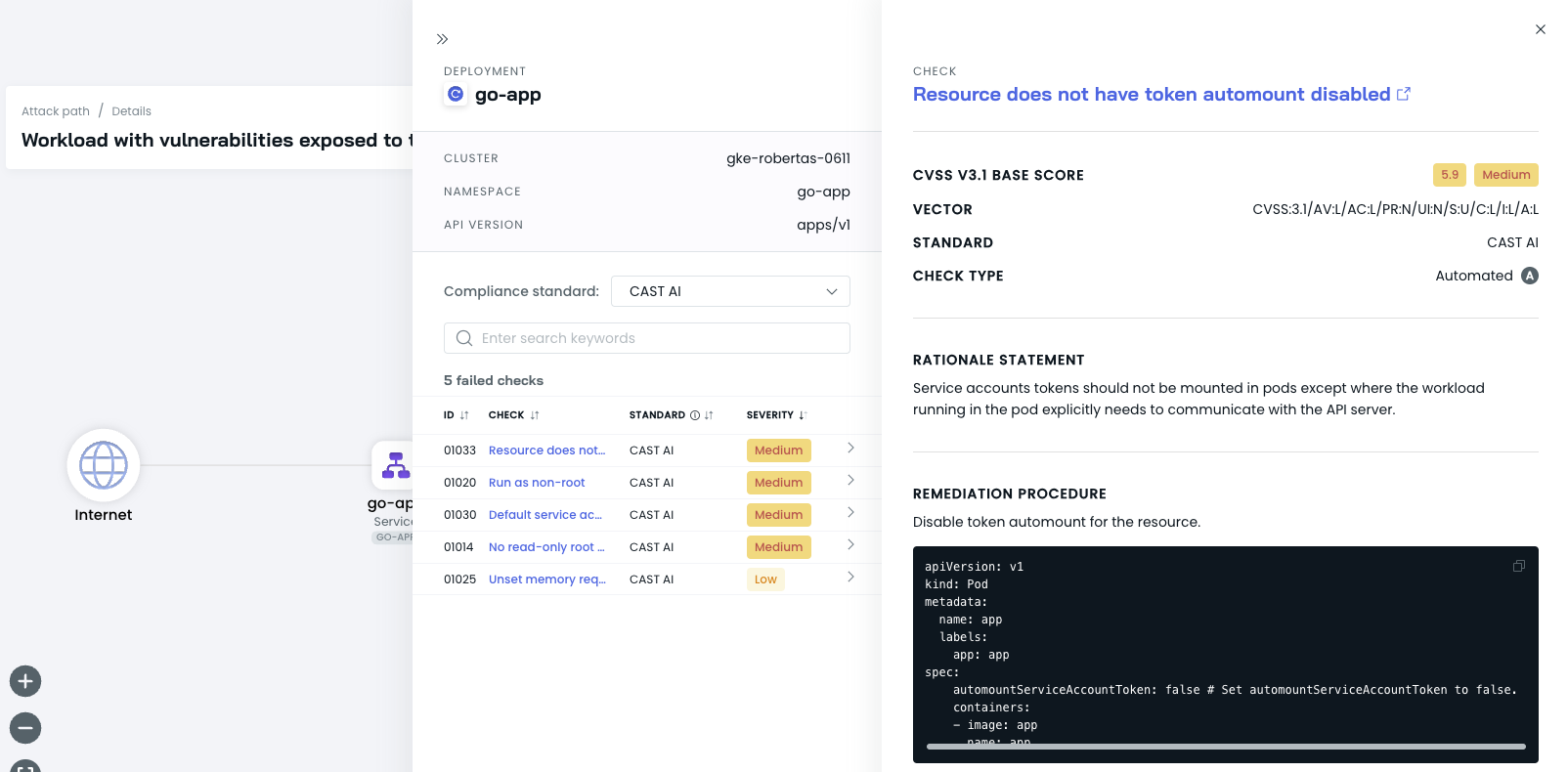
- Click on the Image node in the attack path to view the details of the vulnerable container image.
NoteVulnerable image nodes have a red counter visible in the attack path graph that identifies the number of detected vulnerabilities in the image. This takes priority over any other possible steps in the attack path.
- Review the list of identified vulnerabilities and their severity levels. Click on an issue to view it in detail.
- Take the necessary actions to remediate the vulnerabilities, such as:
- Updating the container image to a version that includes security patches for the identified vulnerabilities.
- Rebuilding the container image with the latest security updates and dependencies.
- Replacing the vulnerable image with a more secure alternative.
- Redeploy the workload with the updated and secure container image.
Attack path generation window
CAST AI generates attack paths for your Kubernetes clusters every 3 hours. This regular scanning ensures you have up-to-date information about potential security risks in your environment.
By refreshing attack path data multiple times per day, CAST AI helps you:
- Stay informed about newly introduced vulnerabilities
- Detect changes in your cluster configuration that may impact security
- Prioritize remediation efforts based on the most current information
Keep in mind that while attack paths are generated every 3 hours, the severity and details of existing paths may change between scans as your cluster evolves or as new vulnerability information becomes available.
Updated 5 months ago
