Compliance
Make sure your cluster configuration follows industry standard best practices for greater compliance
The Compliance report on the Cast AI platform is a powerful tool for assessing the security posture of your Kubernetes clusters against industry and DevOps best practices. The report provides a detailed evaluation of your resources, ensuring compliance with the security and operational standards set by Cast AI or the CIS for Kubernetes benchmarks.
Cast AI employs a transparent scoring system that prioritizes issues based on severity, enabling you to allocate resources effectively and streamline communication with the security team. The severity score and level of each issue are determined using the CVSS v3.1 (Common Vulnerability Scoring System) standard, providing a standardized approach to assessing the criticality of security vulnerabilities.
Access the report
To access the Compliance report, follow these steps:
- Log in to the Cast AI console.
- Select Security > Compliance from the sidebar.
NoteTo receive a full assessment of your cluster, enabling the Cast AI Security feature is required. By default, the Compliance report only provides a limited number of best practices without this feature. Please refer to the Getting started section for instructions on enabling Cast AI Security.
Compliance scanning frequency
Cast AI continuously monitors your cluster configuration for compliance with security best practices:
- Scan frequency: Compliance checks are performed every 60 seconds by default
- Real-time updates: The compliance report reflects near real-time changes in your cluster configuration
- Configuration: The scan interval can be adjusted using the Kvisorconfiguration parameter:
--kube-linter-scan-interval=60s
This frequent scanning ensures that any configuration changes that impact your security posture are quickly identified and reported.
Inside the report
The Compliance report comprehensively lists findings related to best practice violations in your Kubernetes environment. Each check in the report includes detailed information to help you understand and address the issue:
-
Check type: Indicates whether the check is Manual or Automated.
- Manual checks require human intervention to determine if the system's configuration meets the expected state.
- Automated checks can be evaluated automatically against the recommended state using configuration assessment tools, i.e., a pass/fail assessment result can be automatically achieved.
-
Description of the check: Offers a clear explanation of what the check is looking for and why it's important for your cluster's security and performance.
-
Severity level: Based on the Common Vulnerability Scoring System (CVSS), this indicates the potential impact of the issue. Levels range from Low to Critical, helping you prioritize your remediation efforts.
-
Number of affected resources: Provides a count of how many resources in your cluster are impacted by this particular best practice violation, giving you an idea of the issue's scope.
-
Relevant standards and configurations: This section lists the industry standards (such as CIS Benchmarks) and specific configurations related to this check, helping you understand its broader context and importance.
-
Remediation procedure: Offers step-by-step instructions on addressing the issue and bringing your cluster into compliance with best practices.
Report summary
The report is also summarized as a widget in the Security dashboard.
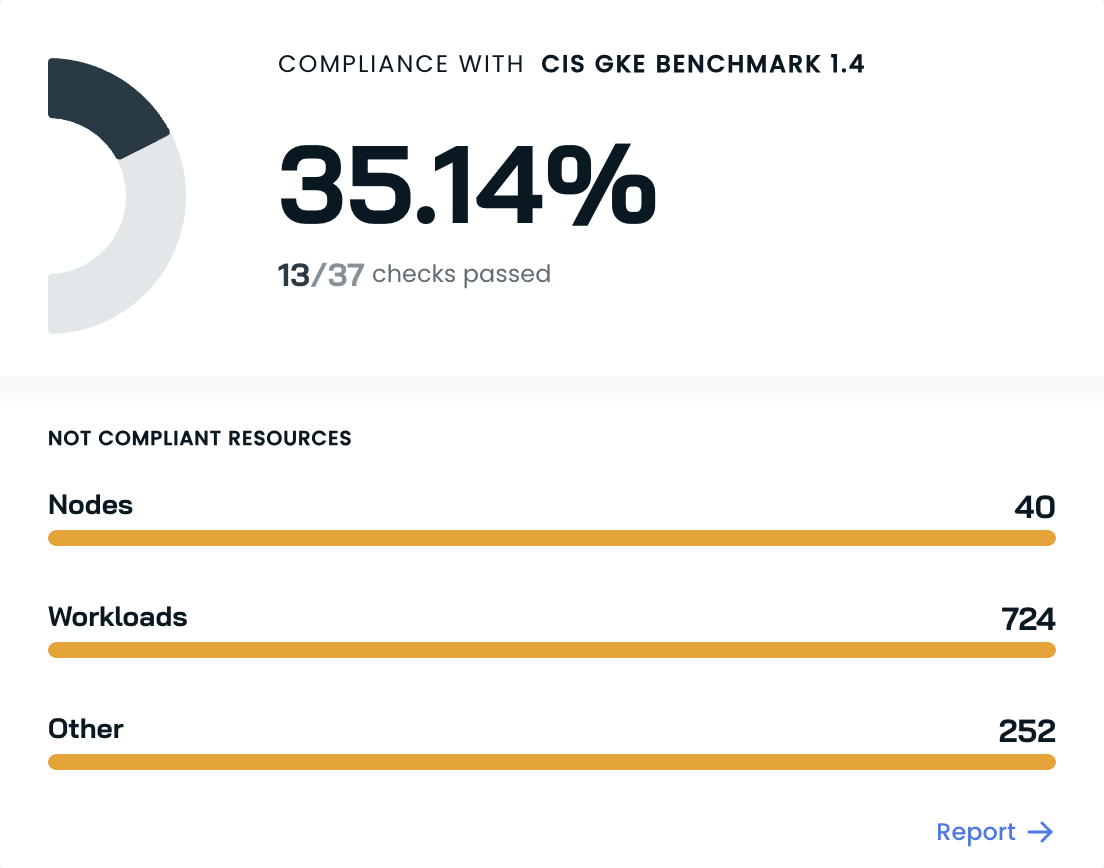
The widget provides a quick overview of your cluster's compliance status:
-
Overall compliance score: Shows the percentage of compliance with a specific benchmark.
-
Checks passed: Displays the number of passed checks out of the total.
-
Non-compliant resources breakdown:
- Nodes: Shows the number of non-compliant nodes
- Workloads: Indicates the number of non-compliant workloads
- Other: Lists other non-compliant resources
-
Link to report: View the full, detailed compliance report.
This summary widget helps you quickly assess your cluster's security posture and identify areas that require immediate attention without first diving into the full report.
Filter resources
To focus on specific resources, use the filters located above the list.
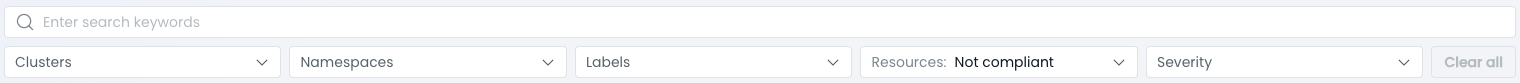
The filters allow you to narrow down the view based on various criteria, such as:
- Resource location (cluster or namespace)
- Resource labels
- Severity level
- Compliance standard
By applying the appropriate filters, you can quickly identify the resources of interest and assess their compliance with best practices.
Access detailed compliance check information
Click on the check name for more information about a specific failed check.
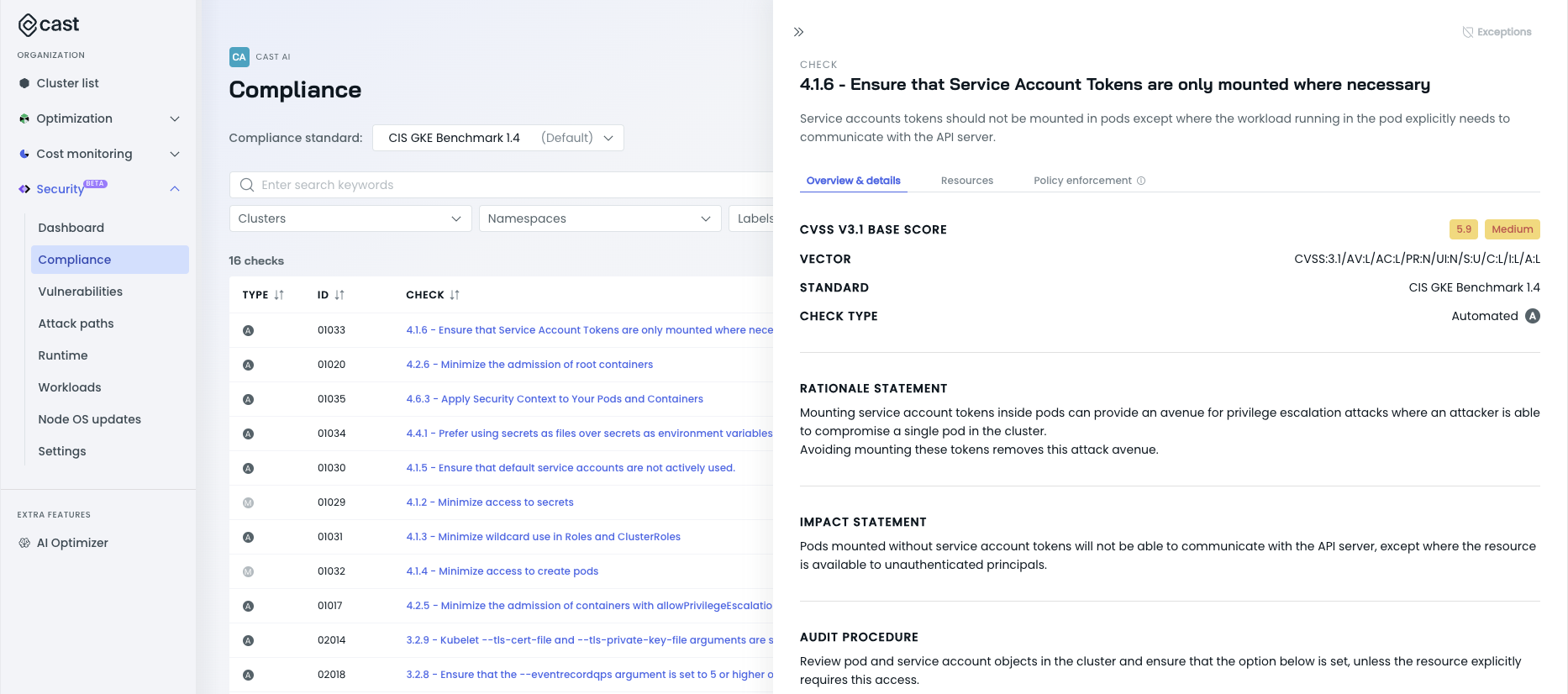
This action will open a detailed view containing the following:
- Comprehensive description of the problem
- Severity level of the issue
- Remediation steps to address the violation
- Number of affected resources
- Resources associated with the check
- Other relevant details
Manage exceptions
Sometimes, you may have resources that do not comply with best practices but are considered acceptable risks. The Compliance report provides an exception feature that allows you to exclude such resources from the reporting.
Add an exception
To exclude specific resources from a compliance check, follow these steps:
- Click on the check you want to manage.
- Click the Exceptions button in the drawer's top right corner.
- In the new drawer that appears, define the exception rules by specifying the location, name, and kind of resource you want to exclude. You can create multiple exception rules as needed.
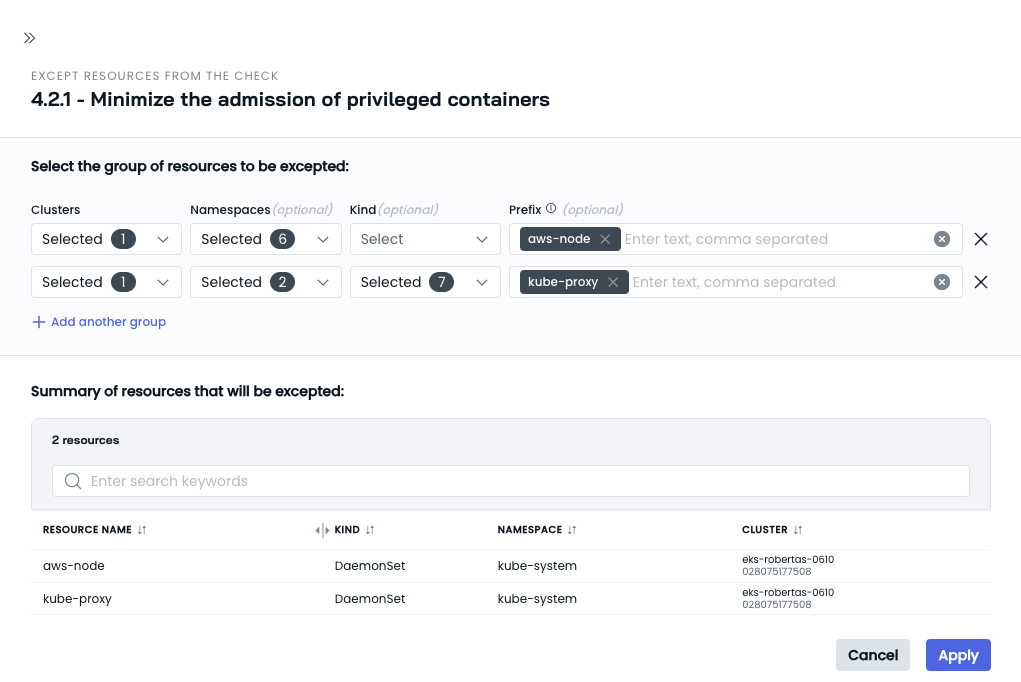
- Review the impacted resources in the table.
- If you are satisfied with the result, click the Apply button to save the exceptions.
To view the excluded resources for each check, select the Excepted value in the Resources filter in the Resources tab:
Remove or modify an exception
If you need to remove previously applied exceptions, follow these steps:
- Click on the check you want to manage.
- Click the Exceptions button in the drawer's top right corner.
- In the exception rules drawer, modify or remove the rules as needed.
- Review the dynamically updated list of excepted resources in the table.
- If you are satisfied with the changes, click the Apply button to save the modifications.
Updated 5 months ago
