Audit log
Check out this page to learn how Cast AI's Audit log tracks and displays detailed records of all operations, policy actions, and changes made in your cluster.
The Audit log provides a detailed view of all actions and events that occur within your cluster managed by Cast AI. This feature helps you track changes, troubleshoot issues, and maintain security compliance by recording both user-initiated actions and automated policy-driven changes.
How to access it
To view the Audit log:
- Navigate to your cluster in the Cast AI console
- Select Audit log from the left sidebar navigation menu
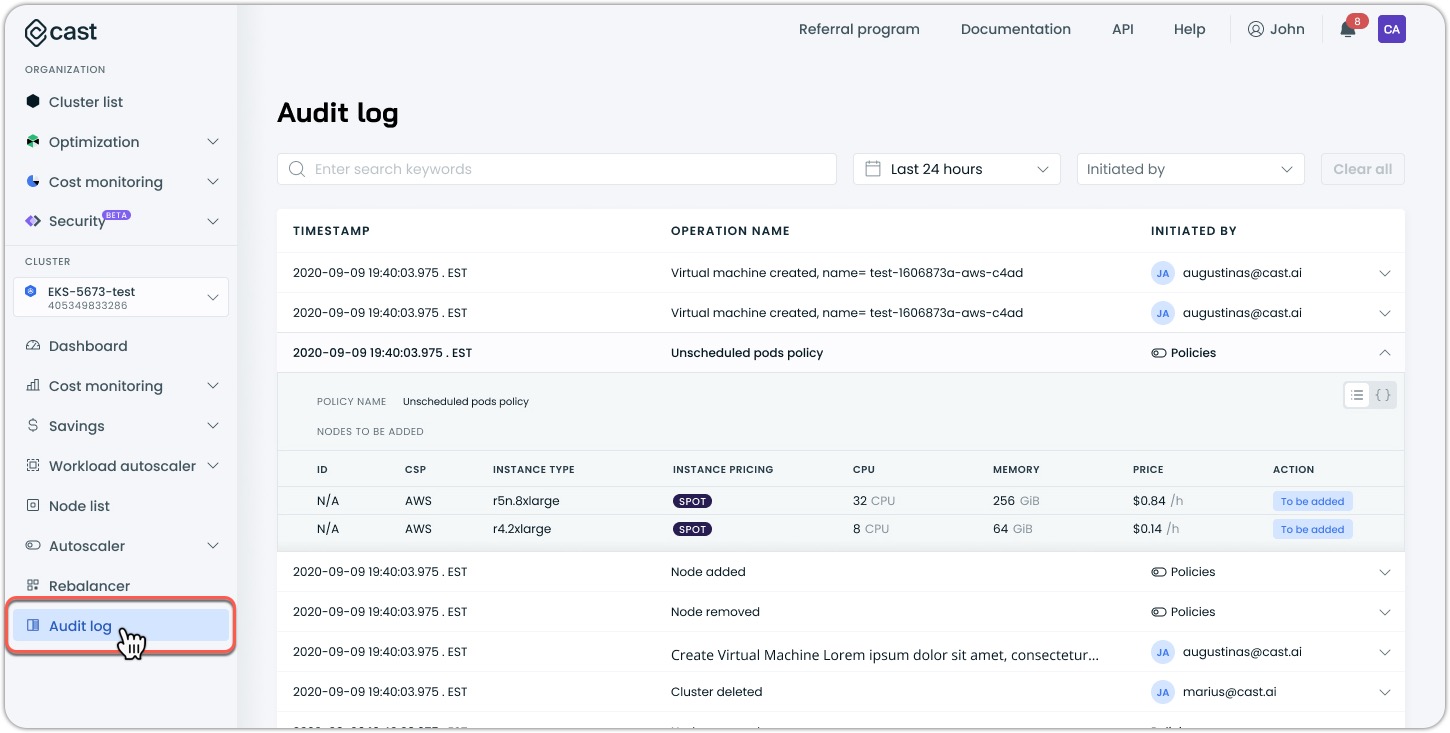
Understanding the interface
The Audit log displays information in a table format with the following columns:
- Timestamp: When the action occurred
- Operation name: Description of the action or event
- Initiated by: Who or what triggered the action (user email or policy)
Each log entry can be expanded to view additional details about the operation:
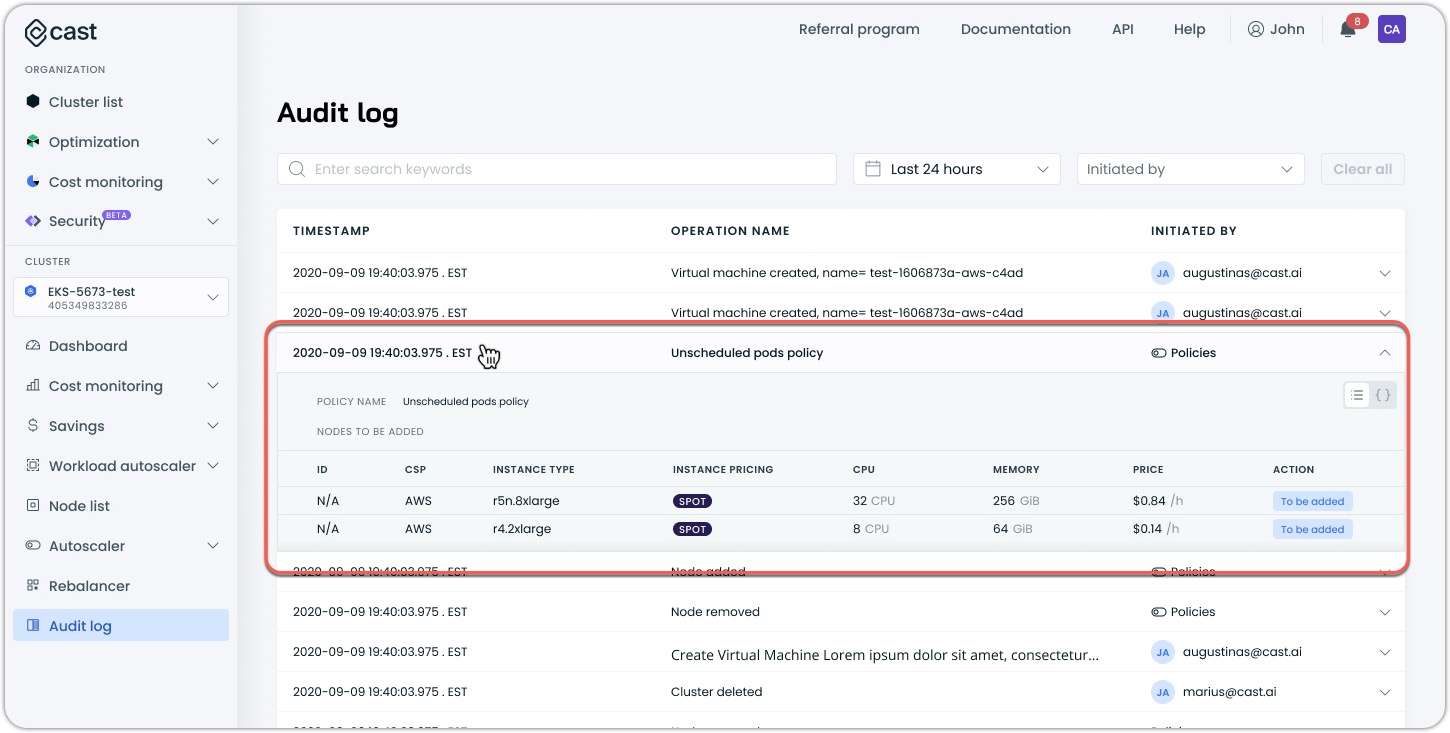
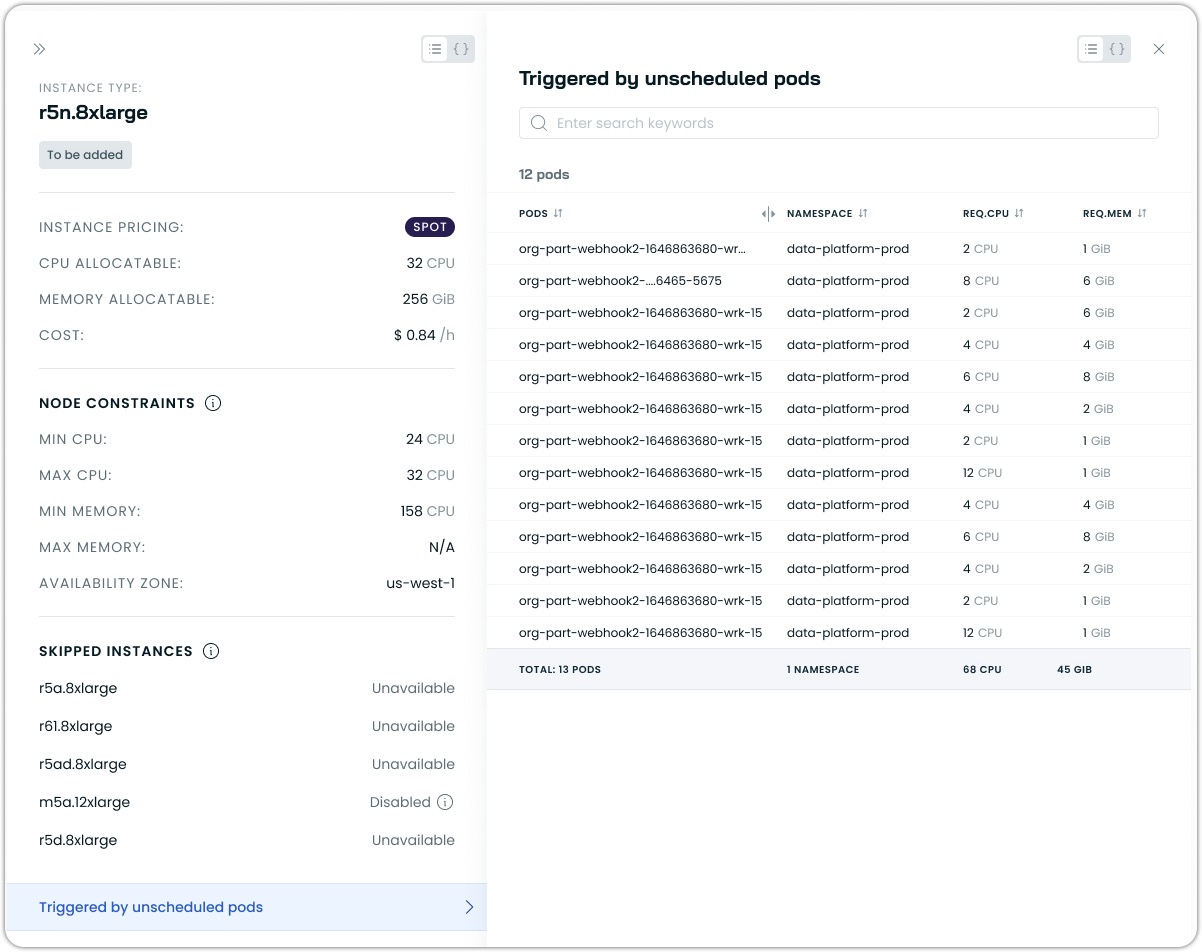
For certain events, like unscheduled pods policy events, you can click on the instance type to view detailed information about:
- Instance specifications
- Node constraints
- List of unscheduled pods that triggered the event
- Resource requirements per pod
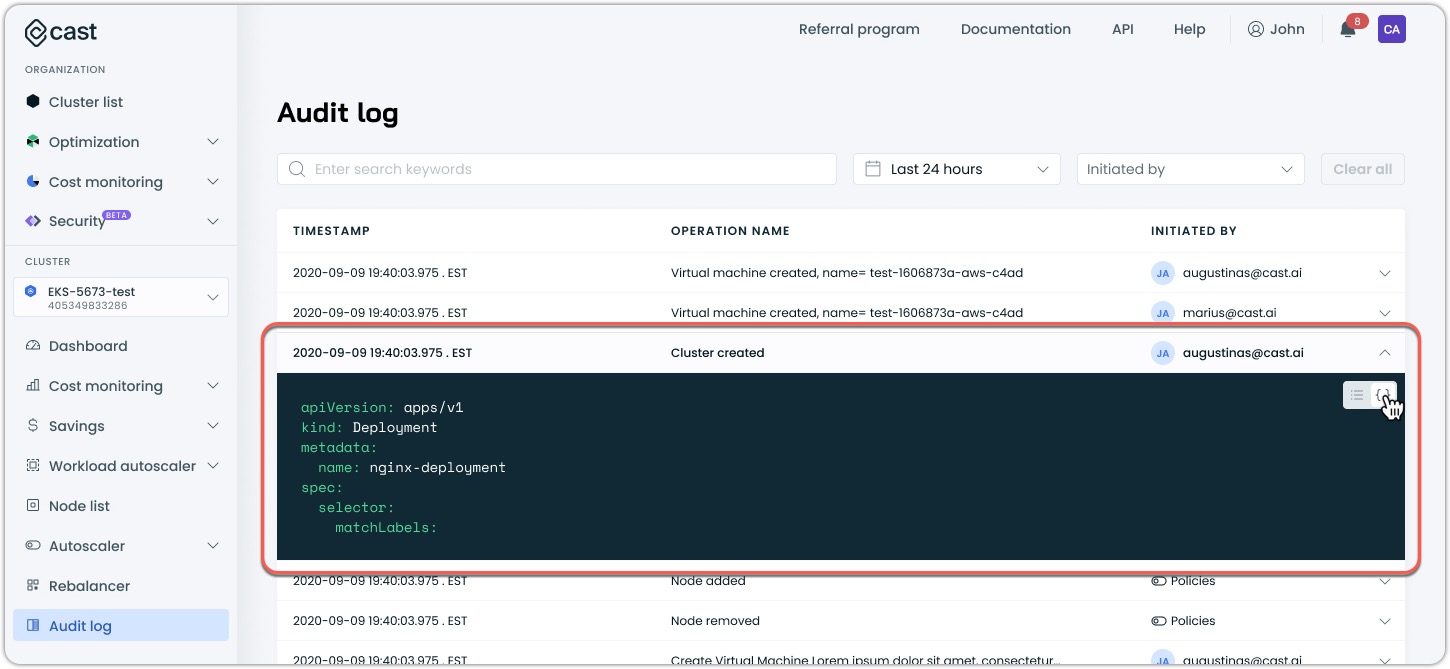
The entry summary can then be viewed as is in this table format, or you can switch to the YAML/JSON view by clicking the { } icon in the top right of the opened row:
Filtering capabilities
The Audit log provides powerful filtering options to help you find specific events:
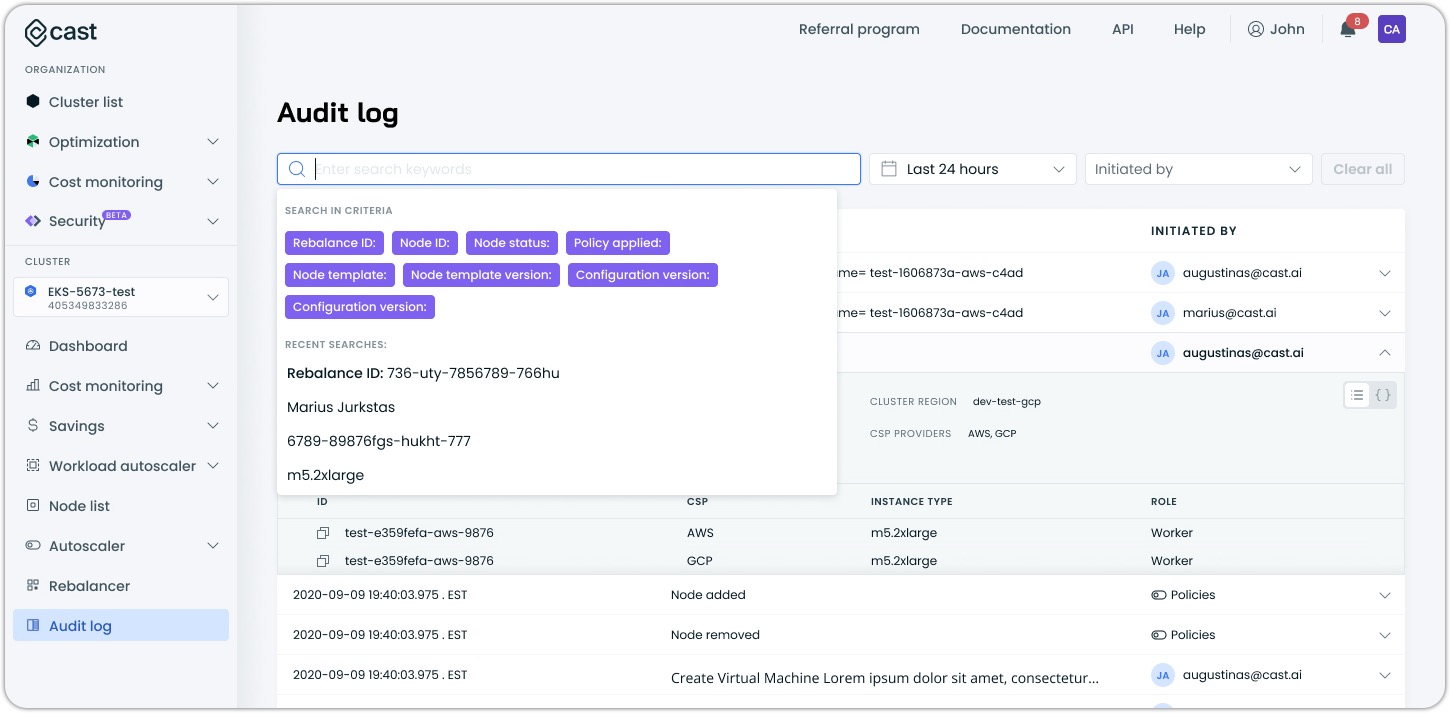
Search filters
- Text search: Enter keywords in the search bar to filter log entries
- Time range: Select from preset time ranges (e.g., Last 24 hours) or specify a custom period
- Initiated by: Filter by specific users or policies that triggered actions
Advanced search criteria
Use the following advanced filters to narrow down results:
- Rebalance ID
- Node ID
- Node status
- Policy applied
- Node template
- Node template version
- Configuration version
Recent searches
The Audit log maintains a list of your recent searches for quick access to frequently used filters.
Types of tracked events
The Audit log tracks various events related to cluster operations, node management, and policy changes. Here's a complete list of events tracked by the system:
| Event Category | Event Type | Description |
|---|---|---|
| Policy Management | Policy enabled | A policy has been activated in the cluster |
| Policy configuration | Changes made to policy settings or parameters | |
| Unschedulable pods policy | Events related to handling pending pods that need scheduling. Click the instance type in the event row to view detailed information about the unscheduled pods that triggered the event. | |
| Node Operations | Node added | A new node has been added to the cluster |
| Node removed | A node has been removed from the cluster | |
| Node deletion requested | A request has been made to delete a node | |
| Add node failed | An attempt to add a node to the cluster has failed | |
| Adding node failed | An alternative event name for failed node addition attempts | |
| Nodes interrupted | Nodes have been interrupted (typically for Spot Instances) | |
| Dead node deleted | Actions taken on nodes determined to be non-responsive | |
| Cluster Management | Cluster created | A new cluster has been initialized |
| Cluster paused | Cluster operations have been temporarily suspended | |
| Cluster deleted | A cluster has been permanently removed | |
| Cluster hibernated | The cluster has been hibernated to reduce costs during inactive periods | |
| Cluster hibernation triggered | A hibernation process has been initiated for the cluster | |
| Cluster hibernation schedule failed | A scheduled hibernation operation has failed to execute | |
| Cluster hibernation job finished | The hibernation process has completed successfully | |
| Cluster hibernation job pending | A hibernation job has been queued and is waiting to be processed | |
| Cluster hibernation job failed | A hibernation job has encountered an error and failed to complete (when expanded, shows the specific operation like "Resumption") | |
| Cluster reconcile triggered | The cluster reconciliation process has been initiated | |
| Autoscaler executed | The cluster autoscaling mechanism has performed an action, the details of which are provided in the log | |
| Rebalance plan change | Modifications to the cluster's rebalancing strategy | |
| Instance Management | Addblacklist executed | Instance types have been added to the blacklist |
| Spot Instance Events | Spot fallback enabled | Spot Instance fallback mechanism has been activated |
| Spot fallback disabled | Spot Instance fallback mechanism has been deactivated | |
| Spot fallback updated | Updates made to spot fallback settings | |
| Spot node found | A suitable Spot Instance has been located | |
| Failed to add nodes | Unable to add Spot Instances | |
| Failed to drain nodes | Unable to safely remove workloads from spot nodes | |
| Pod Management | Unscheduled pods policy | Events related to handling pending pods that need scheduling |
These events provide a comprehensive audit trail of all significant actions and changes within your cluster, enabling effective monitoring and troubleshooting of your Kubernetes environment.
Audit log retention and exporting
Audit logs are retained and accessible in the console for 90 days, after which they are archived (see Audit Log Retention Policy for details). However, if you need to analyze your audit logs externally or maintain them indefinitely, you can use our open-source Audit log exporter. This tool allows you to:
- Export audit logs to your preferred storage solution
- Perform custom analysis of historical data
- Maintain audit logs beyond the retention period
- Integrate audit data with your existing monitoring tools
To learn more about exporting your audit logs, visit our Audit log exporter documentation.
Updated 5 months ago
