Security dashboard
The Security dashboard provides a comprehensive overview of your Kubernetes clusters' security posture, bringing together key metrics and insights from various security aspects in one place. This centralized view helps you quickly assess your security status and identify areas that need attention.
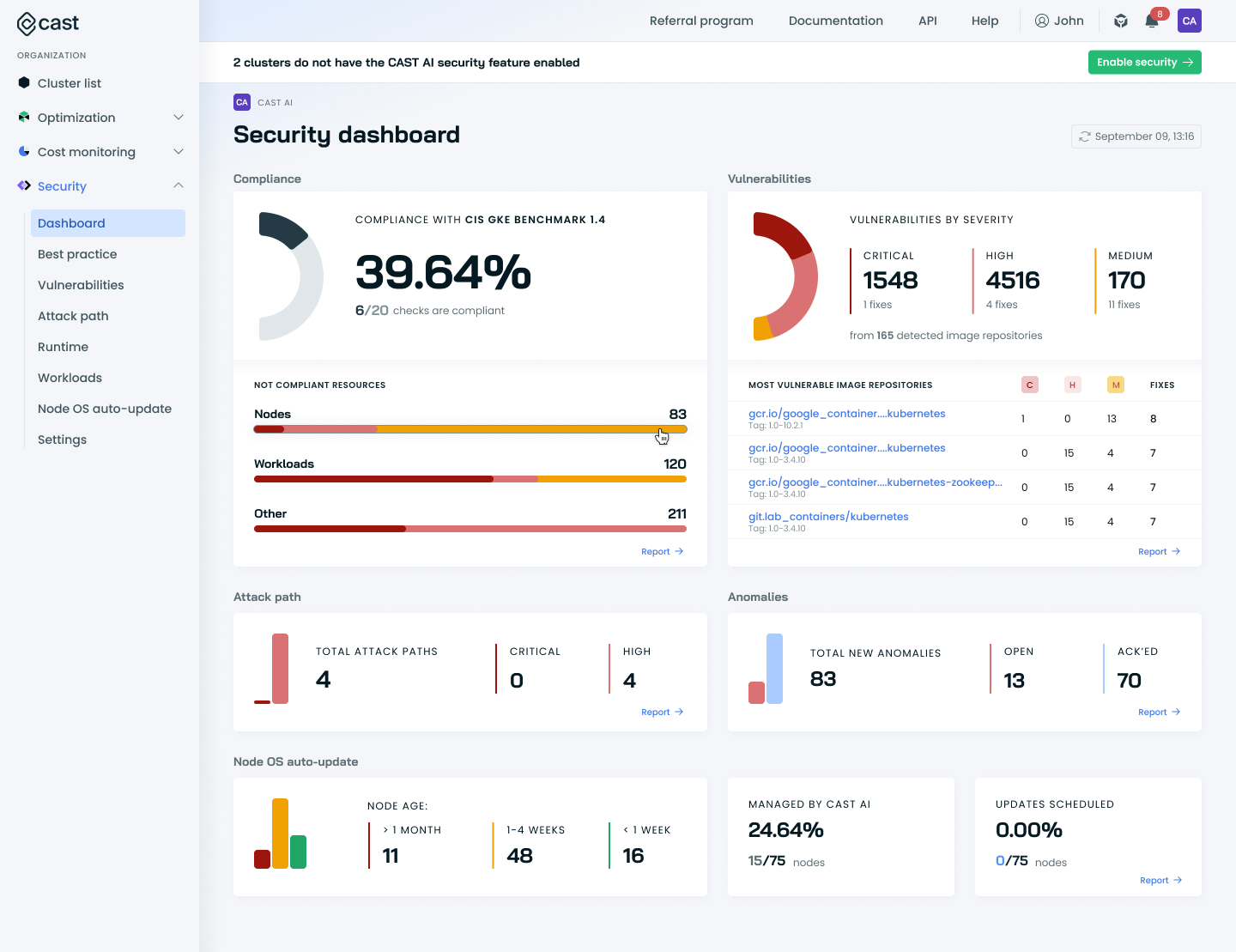
Kubernetes security dashboard
Feature breakdown
Compliance overview
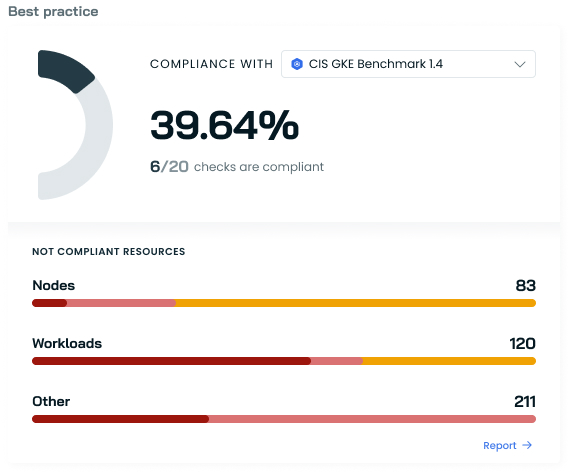
Compliance
The compliance section of the dashboard displays your clusters' alignment with CIS GKE Benchmark standards. It shows:
- Overall compliance percentage
- Number of passed checks out of total checks
- A breakdown of non-compliant resources by category:
- Nodes
- Workloads
- Other resources
The exact benchmark to be used for a compliance check can be selected in the drop-down within the widget, which is especially useful for organizations that utilize multiple cloud providers.
This at-a-glance view helps you quickly identify areas where your organization deviates from security best practices.
Vulnerability management
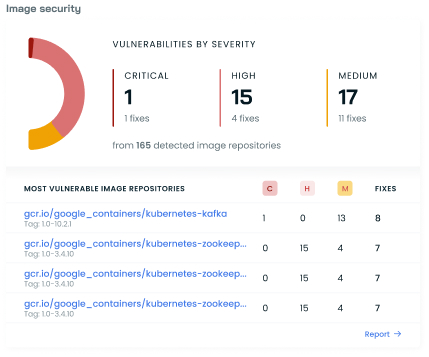
Vulnerabilities
The vulnerability management section presents a clear breakdown of detected vulnerabilities across your environment:
- Distribution of vulnerabilities by severity (Critical, High, Medium)
- Number of fixes available for each severity level
- Total number of affected image repositories
- A list of the most vulnerable image repositories
Attack paths
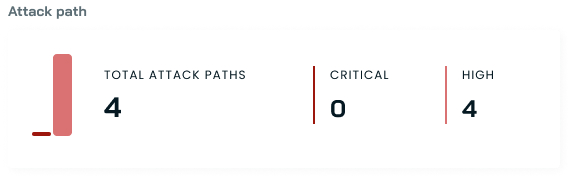
Attack paths
This section provides visibility into potential security vulnerabilities that could be exploited:
- Total number of detected attack paths
- Breakdown by severity (Critical, High)
Runtime anomalies
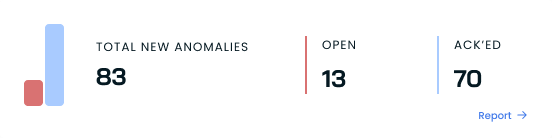
Anomalies
Monitor runtime security events with:
- Total number of detected anomalies
- The distribution between open and acknowledged issues
Node OS auto-update status
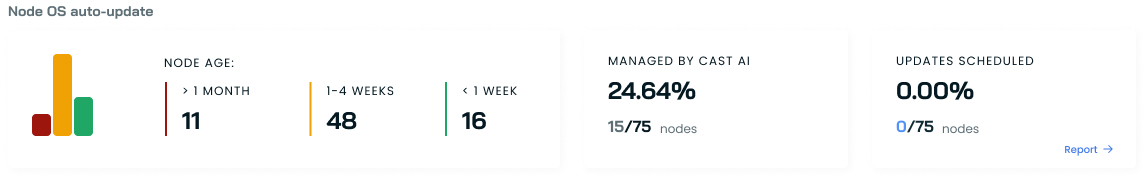
Node OS updates
Track the health and update status of your cluster nodes:
- Node age distribution (> 1 month, 1-4 weeks, < 1 week)
- Percentage of nodes managed by CAST AI
- Update schedule status and compliance
Using the dashboard effectively
The Security dashboard serves as your first stop for security oversight, enabling you to:
- Identify immediate security concerns requiring attention
- Track security trends over time
- Access detailed reports for each security aspect
- Monitor the effectiveness of your security measures
For a detailed analysis of any security aspect, navigate to each section of the Security product separately for comprehensive views of specific security features.
Updated 6 months ago
