Access requirements and permissions
Overview
Before using Cast AI DB Optimizer (DBO), it's important to understand the different types of access required for various features. This page clarifies:
- Network access requirements for the core DBO caching functionality
- Optional cloud provider permissions for AWS RDS Performance Insights
Network Access Requirements
The core DBO caching functionality only requires:
- Network connectivity between your Kubernetes cluster (where DBO is deployed) and your database
- Standard database connectivity (the same level of access any application would need)
No special database permissions are required for the caching functionality to work. DBO simply acts as a proxy between your applications and your database.
Cloud Provider Permissions (Optional)
AWS Permissions for Performance Insights
The permissions described below are only required if you want to use the Performance Insights features with AWS RDS. These permissions allow Cast AI to collect performance metrics to show you data about your database performance in the console.
NoteThese permissions are on your AWS account, not on the database itself. They allow read-only access to metrics and do not permit Cast AI to modify your database in any way.
When connecting your AWS RDS instances to Cast AI for Performance Insights, you must grant permissions through a cross-account IAM role. This role allows Cast AI to access necessary metrics and information while maintaining security best practices.
Required AWS-managed policies
The following AWS-managed policies must be attached to the IAM role:
Custom policy for Performance Insights
When accessing Performance Insights APIs, Cast AI requires permission to decrypt the data using the kms:Decrypt action. Add the following custom policy to your IAM role:
{
"Version": "2012-10-17",
"Statement": [
{
"Action": "kms:Decrypt",
"Resource": "*",
"Effect": "Allow"
}
]
}Trust relationship configuration
The IAM role must have a trust relationship that allows Cast AI to assume it. Configure the following trust policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::891377030120:user/dbo-poller-prod"
},
"Action": "sts:AssumeRole"
}
]
}Verifying permissions
You can verify your IAM role configuration using the AWS Management Console or AWS CLI.
Using AWS Management Console
-
Open the IAM console
-
Navigate to Roles and select your Cast AI role
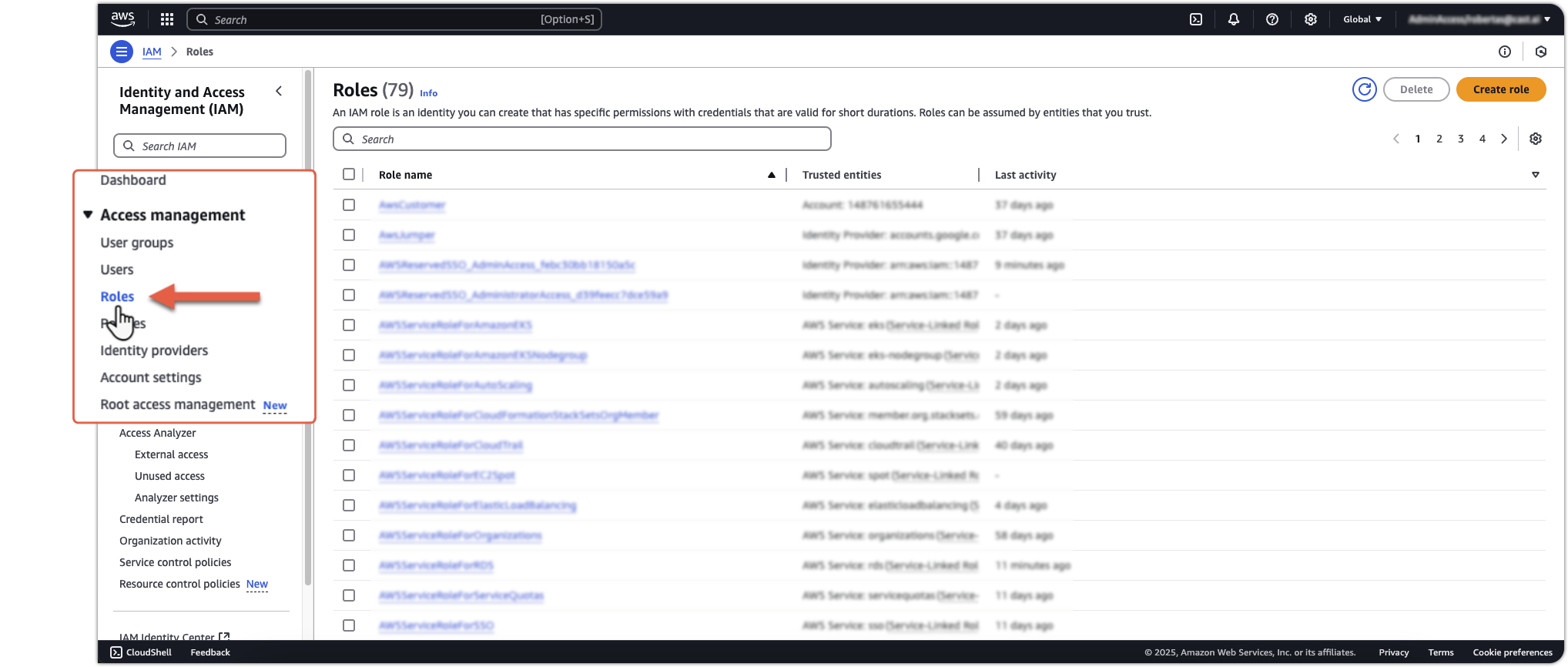
-
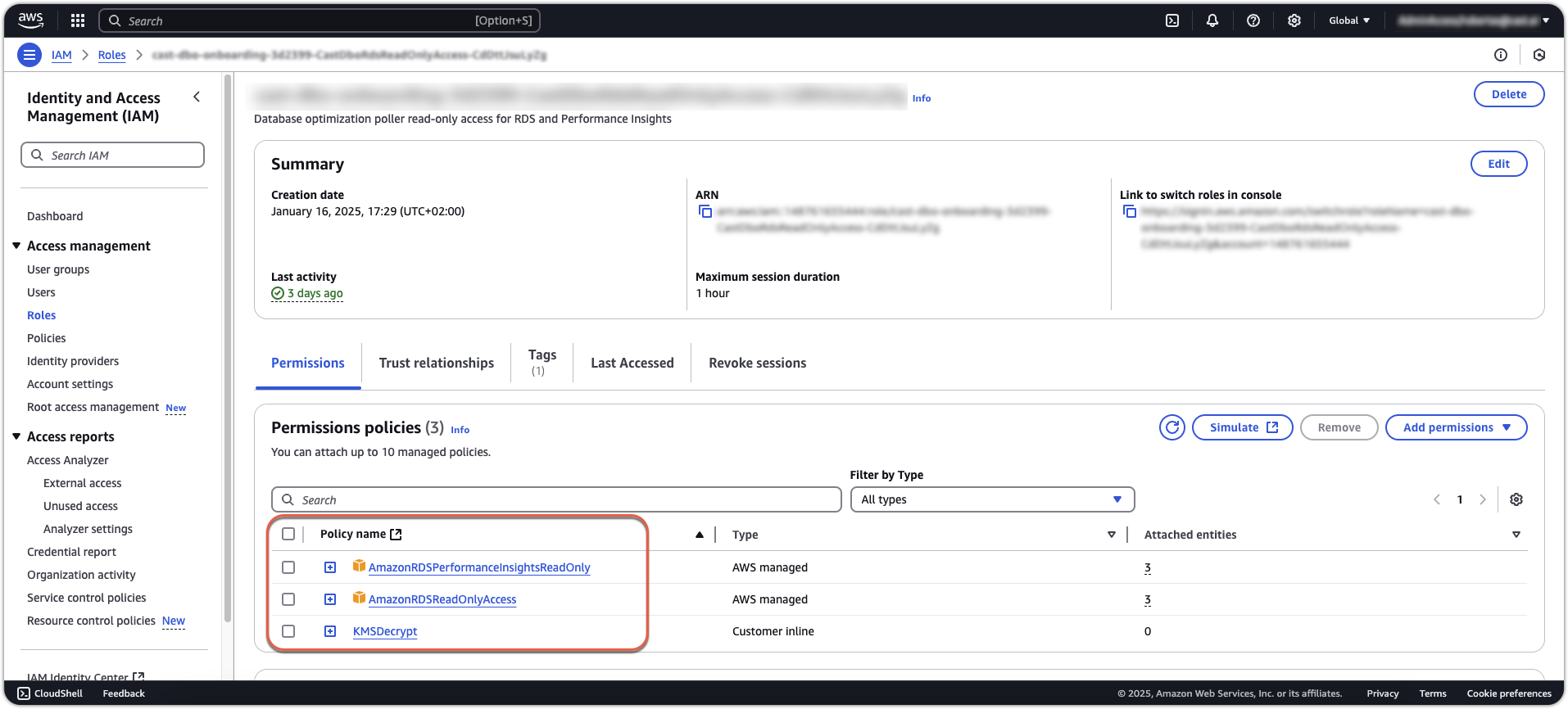
In the Permissions tab, verify that these policies are listed:
AmazonRDSPerformanceInsightsReadOnlyAmazonRDSReadOnlyAccess- Your custom KMS Decrypt policy
3.
-
Select the Trust relationships tab
-
Confirm the trust policy includes the Cast AI principal:
"AWS": "arn:aws:iam::891377030120:user/dbo-poller-prod"
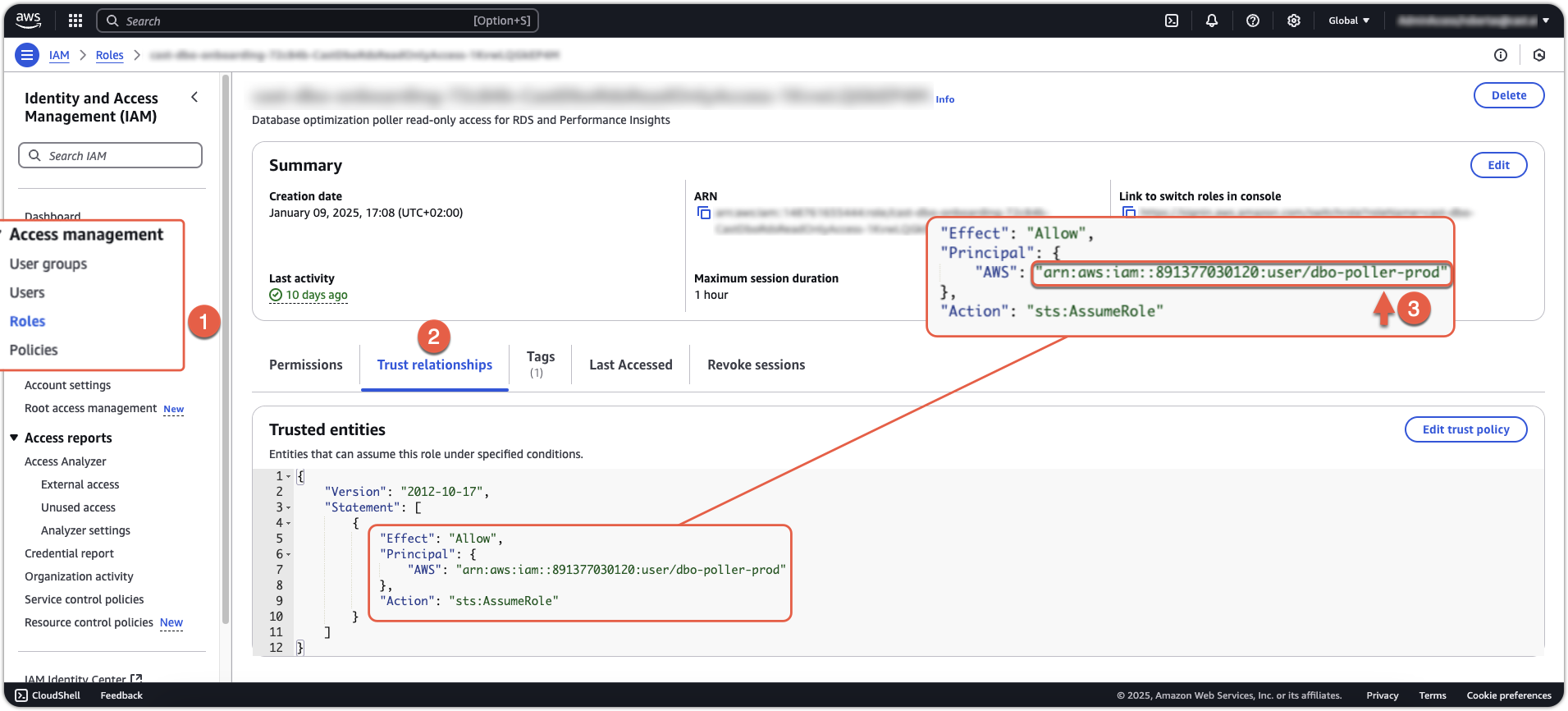
Using AWS CLI
- Check the attached policies:
aws iam list-attached-role-policies --role-name <your-role-name> aws iam list-role-policies --role-name <your-role-name> - Verify trust relationship:
Look for the
aws iam get-role --role-name <your-role-name>AssumeRolePolicyDocumentin the output to confirm the trust relationship.
Security and Data Access
Cast AI takes data security seriously:
- These permissions are read-only and do not allow Cast AI to modify your database configurations
- Cast AI does not access the actual data within your databases
- For the caching functionality, all data remains within your infrastructure
- Only anonymized metadata about query patterns is sent to the Cast AI control plane
For more information about how Cast AI handles your data, see our Security and Compliance documentation.
Updated 5 months ago
