Security reports
Introduction
Maintaining a secure Kubernetes configuration can be challenging, especially when dealing with extensive and complex setups. To help you overcome this challenge, Cast AI provides comprehensive Security Reports that allow you to scan your clusters for vulnerabilities and assess them against industry best practices. The reports generated by this feature offer actionable insights to help you identify and resolve detected issues.
Cast AI's Security Reports ensure that your organization's Kubernetes security and DevOps configuration adhere to established best practices. The feature provides a consolidated view of all images currently running across your organization's clusters, along with associated vulnerabilities, regardless of the cloud service provider (AWS, Azure, or Google Cloud).
Security Reports are available to all users who have onboarded their clusters to Cast AI and enabled the Security feature. To read more about enabling the Cast AI Security component, read the Getting started section.
Organization-level security reports
To access the list of clusters onboarded to the Security solution, navigate to the Security > Settings section of the Cast AI console. Currently, Cast AI offers the following organization-level reports:
- Assesses your clusters against industry best practices and provides recommendations for improvement.
- Helps you identify and remediate configuration issues that may compromise the security of your Kubernetes environment.
- Scans all container images running across your organization's clusters and identifies vulnerabilities.
- Provides a comprehensive overview of image security, enabling you to take proactive measures to address potential risks.
- Monitors the age of nodes on your cluster and provides automation capabilities for keeping them up to date.
- Helps you maintain a secure and stable Kubernetes environment by ensuring that your nodes are running the latest security patches and updates.
- Identifies potential attack paths within your Kubernetes cluster based on the configuration and network topology.
- Provides insights into the possible ways an attacker could exploit vulnerabilities and gain unauthorized access to your cluster resources.
Please refer to the dedicated pages for each report to learn more about their specific features, benefits, and usage instructions.
Security workloads view
The Security workloads view provides a consolidated list of all workloads across your clusters from a security perspective. This view helps security teams and operators monitor and manage workload security more effectively.
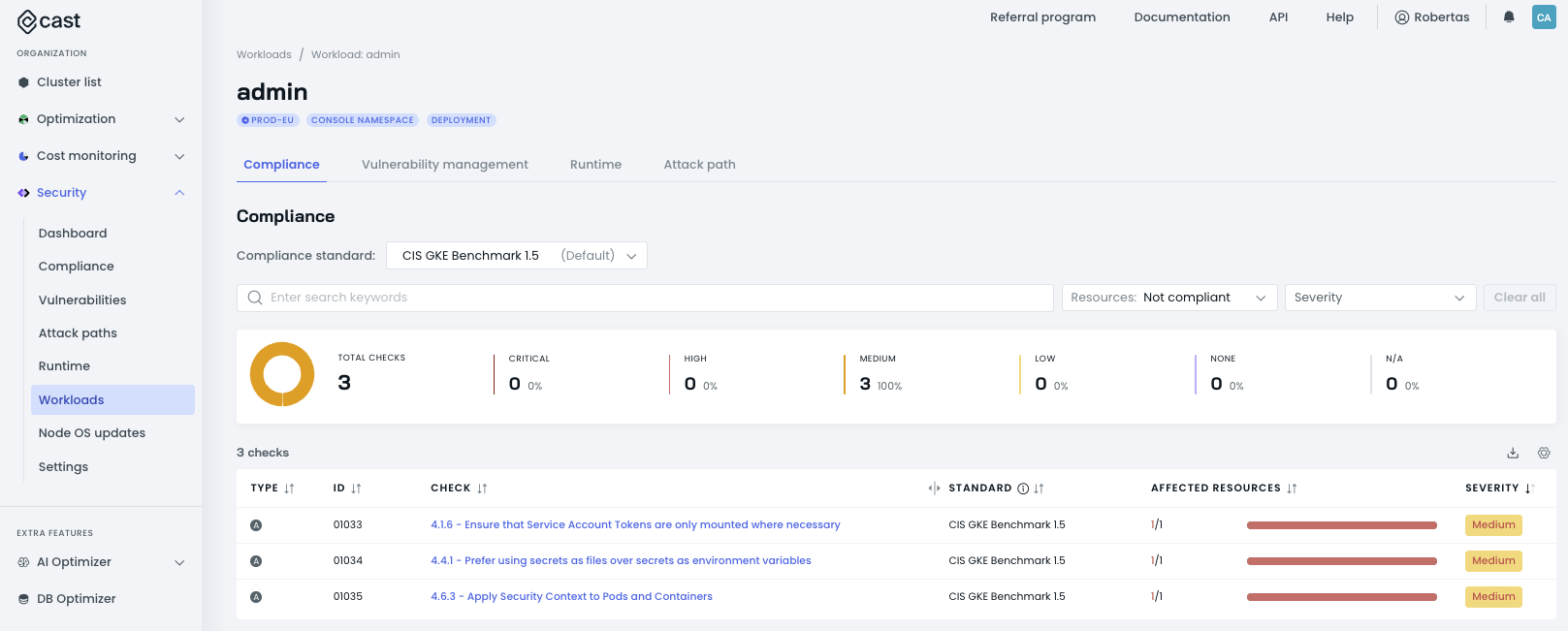
Key features
- Global search: Quickly find specific workloads using the search functionality
- Advanced filtering: Filter workloads by cluster, namespace, or label
- Sortable columns: Order workloads by name, type, cluster, or namespace
- Detailed information: View comprehensive details about each workload's security status
Using the workloads view
The workloads view complements other security features by providing the following:
- Quick access to workload-specific security information
- The ability to identify patterns or issues across similar workloads
Use this view in conjunction with other security features, such as vulnerability scanning and compliance checking, to maintain a strong security posture across your entire Kubernetes environment.
Version for users with the read-only agent installed
If you have connected your cluster to Cast AI using the read-only agent, you can access a limited version of the Best Practice report and Node OS updates automation report without the ability to schedule periodic updates.
To generate these reports, we use the cluster state data from the read-only agent. This agent is the one that connects your cluster to Cast AI, so you don't need to take any additional steps to activate the report.
Updated 4 months ago
