Getting started
Welcome to Cast AI's security offering! Our platform provides an advanced set of automated features designed to enhance the security posture of your Kubernetes clusters. This guide will walk you through enabling and utilizing these features to secure your cluster effectively.
By default, Cast AI offers customers an organizational-level Compliance report that provides valuable insights into your cluster's security posture. However, we recommend enabling the Security feature set on your cluster to unlock the full potential of Cast AI's security assessment capabilities.
Enabling Security is a simple process that grants you access to a wide range of advanced security assessments, including:
- CIS Benchmarks: Evaluate your cluster's compliance with industry-standard best practices.
- Vulnerability management: Identify potential vulnerabilities in the container images running on your cluster.
- Attack paths: See a list of detected attack paths in your Kubernetes clusters that could be exploited. Take proactive measures to mitigate these risks and strengthen your cluster's security posture.
- Node OS updates: Monitor the age of your nodes and schedule automatic updates to ensure your nodes have the latest security patches and remain protected against vulnerabilities.
Enable Security
To enable automation of the Security feature set on your cluster, you must opt in to use deeper security insights. Cast AI will then install the Kvisor security agent to provide enhanced security assessment capabilities.
NoteFor first-time users, we recommend familiarizing yourself with the Getting Started and Enable Automation sections to learn more about cluster onboarding. If you are already familiar with the CAST AI product, follow the steps described below.
Install via Cast AI console
The exact flow for enabling Security depends on whether you have already enabled Cast AI in your connected cluster.
Enable Security with the advanced automation & cost monitoring feature set
If you haven't enabled Cast AI on your cluster yet, follow these steps:
- Log in to the Cast AI console.
- Navigate to your connected cluster and click the
Enable CAST AIbutton in the top right corner.
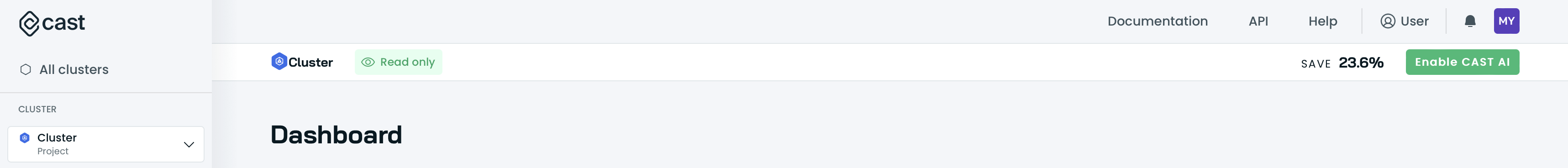
- In the script generation pop-up, ensure that the
Securitybox is checked:
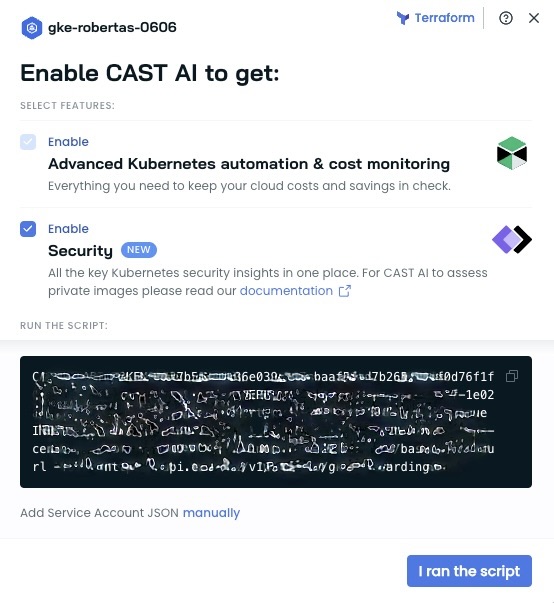
- Copy the generated script and run it in your cluster's command-line interface.
- Once the script execution is complete, click
I ran the scriptto confirm the installation.
Enable Security on a cluster with Cast AI already enabled
If you have already enabled Cast AI on your cluster and want to enable and leverage the Security features, follow these steps:
- Log in to the Cast AI console.
- Go to the
Securitysection in the sidebar. - Click on either the
Enable securityorEnable CAST AIbutton.
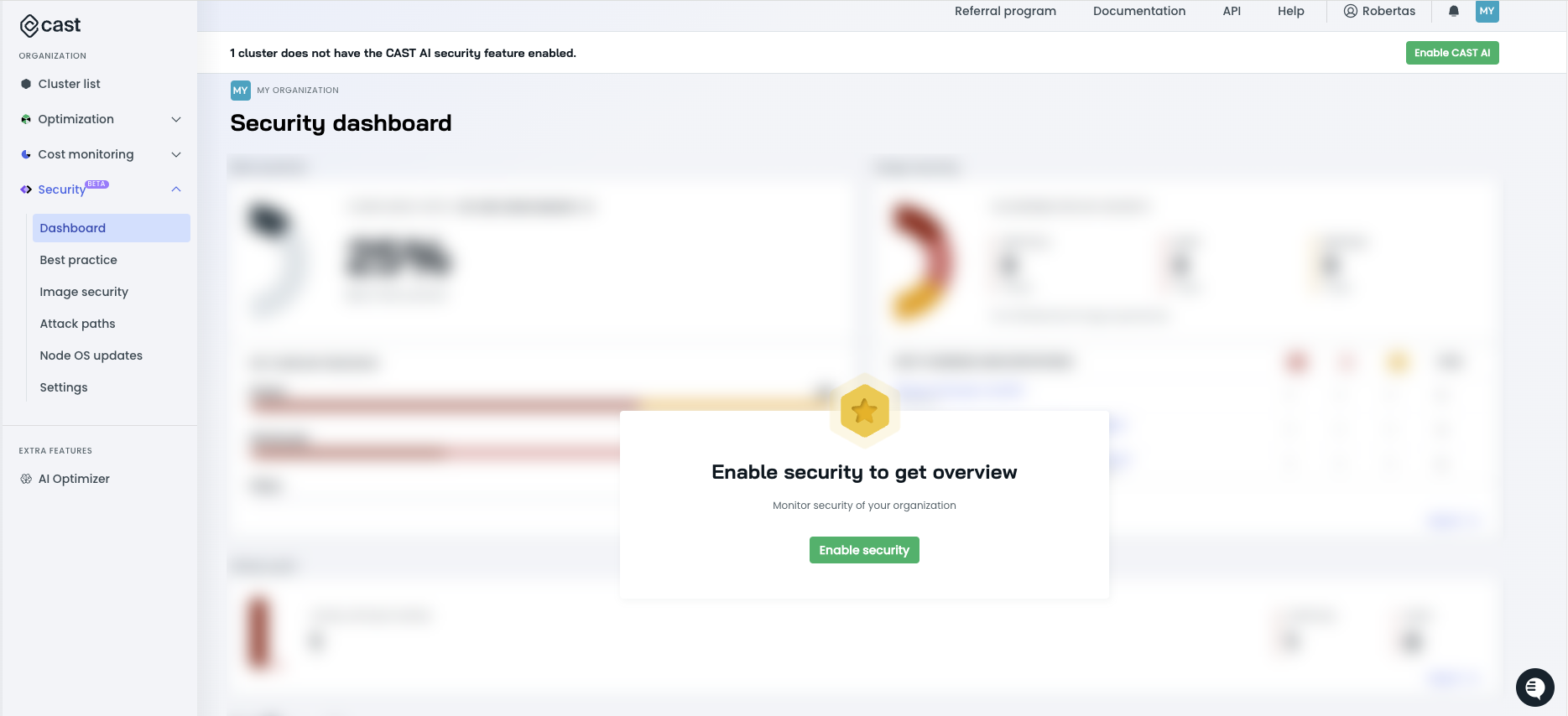
- Choose the cluster for which you want to enable the Security feature set and click
Enable.
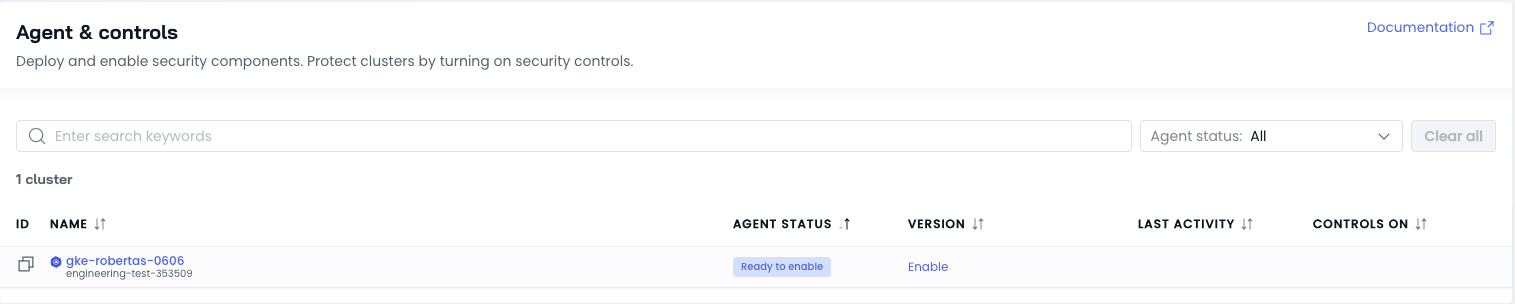
- Copy the generated script and run it in your cluster's command-line interface.
- Once the script execution is complete, click
I ran the scriptto confirm the installation.
The script installs the Kvisor security agent on your cluster, which enables the security feature set.
Installation via Helm or Terraform
You can install the Kvisor security agent using Helm charts or Terraform. Please refer to the Kvisor security agent page for installation instructions.
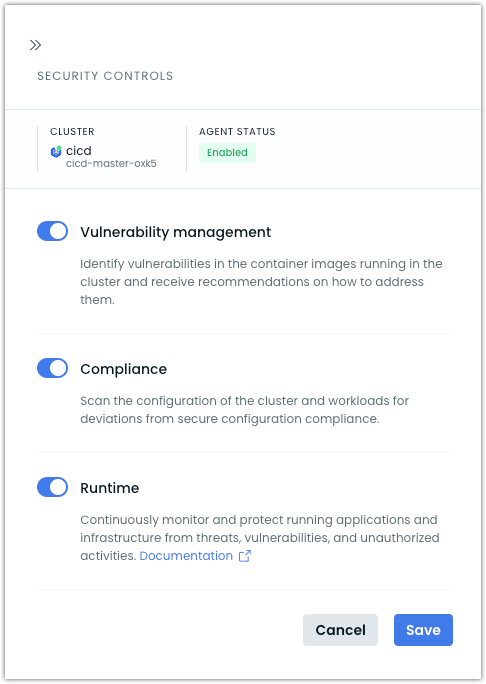
Security controls
By default, the following security controls are enabled automatically for your cluster:
| Control | Description |
|---|---|
| Vulnerability management | Identify vulnerabilities in the container images running in the cluster and receive recommendations on addressing them. |
| Compliance | Scan the configuration of the cluster and workloads for deviations from secure configuration best practices. |
| Runtime | Monitor cluster activities in real-time to detect potential security threats, suspicious behaviors, and security violations during workload execution. |
These controls can be toggled on or off per your organizational requirements.
Status indicators
When viewing your security agent status and controls, you may see the following status indicators:
- Ready to enable - Kubernetes Security is ready to be enabled for the cluster, but the agent is not yet installed
- Enabled - Agent installed and Kubernetes Security enabled for the cluster
- Update needed - A newer version of the security agent is available and should be installed
- Activating... - It may take up to 5 minutes to activate security controls in your cluster after toggling any of them on or off
NoteIf the
Activating...status persists for longer than 5 minutes, there might be a mismatch between the controls that should be enabled and what is actually running in your cluster. In such cases, please contact CAST AI support for troubleshooting assistance.
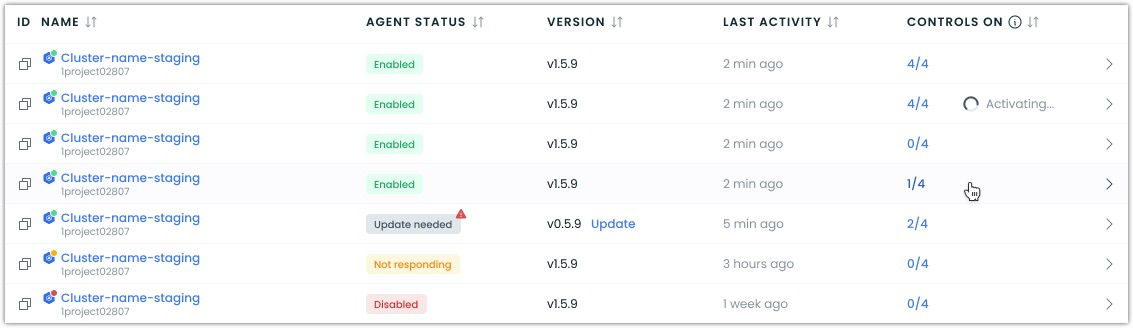
Security Agent status and controls
NoteFor clusters onboarded using Terraform, Security controls can only be enabled or disabled through Terraform configuration. The UI controls for toggling vulnerability management and compliance configuration scanning will be read-only for these clusters. To make changes, update the relevant settings in your Terraform code. This ensures that the desired security control configuration is consistently managed through your Infrastructure as Code (IaC) workflow.
Managing security controls
To manage which controls you want to enable or disable:
- Go to
Security>Settingsin the sidebar - Click on the row of the cluster for which you intend to toggle security controls
- Make desired adjustments and save your changes
Updated 5 months ago
